What is modern encryption ?
Usually, when you want to send someone a message you want to keep it secret from other people who are involved in the transfer process or have access to it. Encryption is a process that helps to keep your information secret. Only those who have a special encryption key can decrypt and read the message.
Modern encryption transforms parts of the message or symbols from which it consists of in other symbols. Moreover, the encrypted message should be as much as possible unstructured and chaotic for a person who is trying to hack a cipher. But modern communications means that are used massively are standardized and therefore limit the capabilities of ciphers, which also need to be standardized. And this is the price that we pay for the opportunity to transmit messages to anywhere in the world.
Today, there are many people who can access the process of transferring your encrypted message and hack it. In "wired" networks, there is an opportunity to redirect the message and hide/confuse the transfer process, but in wireless communication, everyone who wants will be able to catch radio wave and gain access to this process.
But what if there is a way to hide wireless connection or make it obscure. How can this be done?
This can be done by changing the physical layer (OSI model) implementation of communication devices which are involved in the transmission of an encrypted message or by means of Physical Layer encryption.
But what if there is a way to hide wireless connection or make it obscure. How can this be done?
This can be done by changing the physical layer (OSI model) implementation of communication devices which are involved in the transmission of an encrypted message or by means of Physical Layer encryption.
PHY Layer Encryption
Generally, this is set of arrangements that complicate data reception process on unauthorized devices. Unauthorized devices can’t even acquire binary or M-ry data from the received signal that is PHY encrypted and it is recognized as noise or interference. Thus, PHY layer encryption not only encodes data but also forms modulator/demodulator and can be realized only by Software Defined Radio (SDR).

There are two types of PHY layer encryption:
- First for devices that are located in equal signal propagation conditions. For example, simple modulation/keying methods ASK, FSK, PSK, QAM, OFDM and most advanced – precoded OFDM. But it is not widely used because it is not much different from common encryption at higher OSI layers which are widely used.
- Second for devices that located in positions with different signal propagation conditions or operate in channels with high fading. For example, beamforming or space-time encoding for MIMO. But it is not widely used because techniques that are part of it are more often used for establishing of multi-user access and compatibility than for specific data protection.
These methods do not have the main property of crypto coding - they do not have a mechanism that can realize a unique physical layer of the transceiver by a unique crypto key.
And, We've developed the new technique of real PHY Layer Encryption without these flaws.
And, We've developed the new technique of real PHY Layer Encryption without these flaws.
Our Solution
The Company PHY layer encryption technology belongs to the first type and based on DSSS-CDMA. The core element of our technology is the technique that generates orthogonal code sets for DSSS from an arbitrary number. Thus, an almost infinite quantity of orthogonal sequence sets from arbitrary numbers can be created. For example, for a spreading factor of 1024, the number of non-overlapping sets is 21013. Thereby, the arbitrary number that specifies the sequence set is the key for PHY layer encryption. All these sets are quasi-orthogonal to each other and can be used in DSSS processing schemes.
The rule of generation of a limited number of spreading sequence sets with good correlation and low mutual interference has been created. And for spreading factor of 1024 that is used in our modems # of good sequence sets is more than # of possible devices in IPv6 network. Herein, the probability of significant mutual interference (sets overlapping) is lower or equal than BER in AWGN channel.
Thus, presented technology enables to generate unique modulator and demodulator for secure DSSS-CDMA communications from an arbitrary number or key. And it can provide unique PHY layer realization for each or all possible devices in IPv6 network for mass open wireless communications. Thus, this is a real PHY layer encryption that can provide mass secured communications. And it is classified as a polyalphabetic cipher. Additional mixing of serial numbers of sequences in the set can be used to increase crypto protection. The general scheme of a wireless link with PHY Layer encryption that is realized in our modems for multichannel comm is shown in next figure.
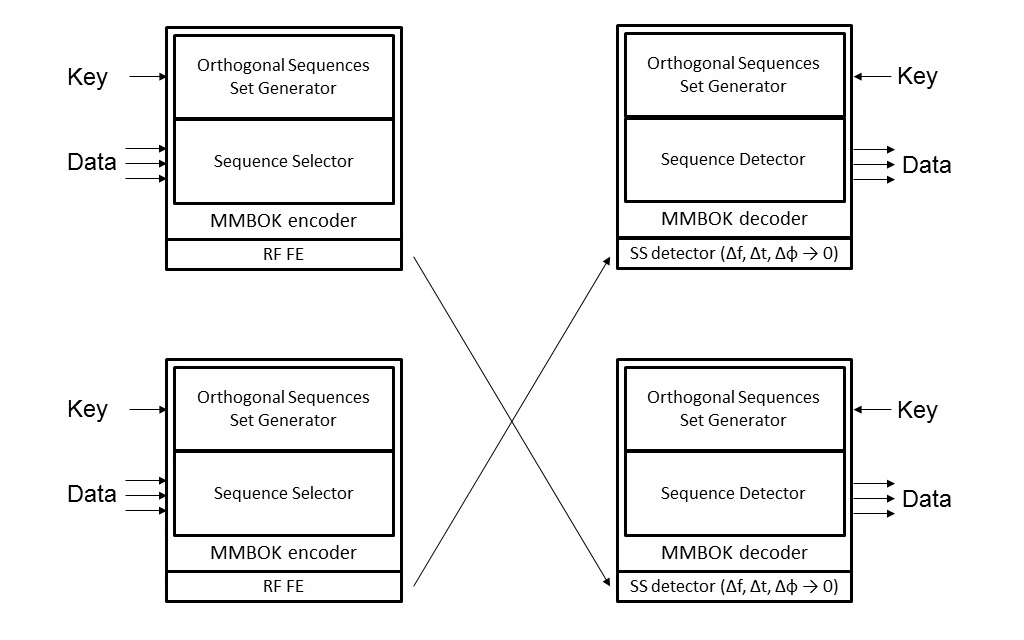 General features of the Company PHY Layer encryption:
General features of the Company PHY Layer encryption:-
Identification. A receiver can identify transmitter if it knows some pool of keys. And you can transfer data to a specific device.
-
Information protection. You cannot even receive a signal if you do not know the key.
-
Ability to provide resistance to interference due to it DSSS nature. And as consequence ability to provide independent multi-user interaction or wireless networks separation when joint frequency resource is used in the same area (other user act as interferences).
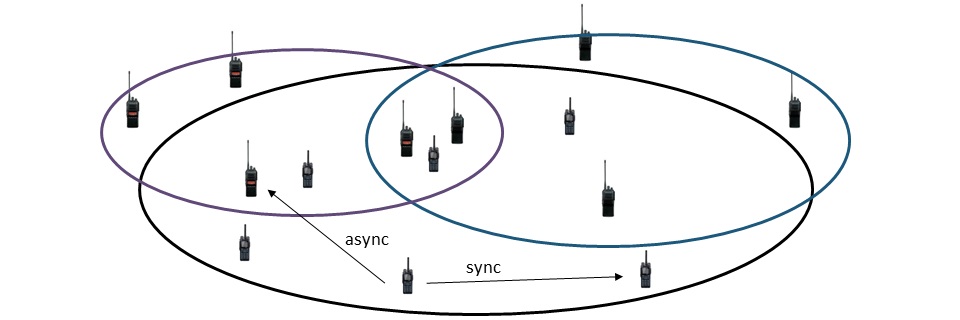
Thus, our encryption technology grants to deploy several CDMA networks in some limited area and use same frequencies at the same time. And devices in different networks can operate independently or asynchronously, but in one network – synchronously as usual CDMA scheme.

Trials
First, let's see how the detector reacts on received signal when it applies the target key (green line), the key from the same set (violet), key from another set (random key - orange). Results of this trial are shown in the figure below, where top figure displays time position value of DSSS waveform and bottom - a value of detector response.
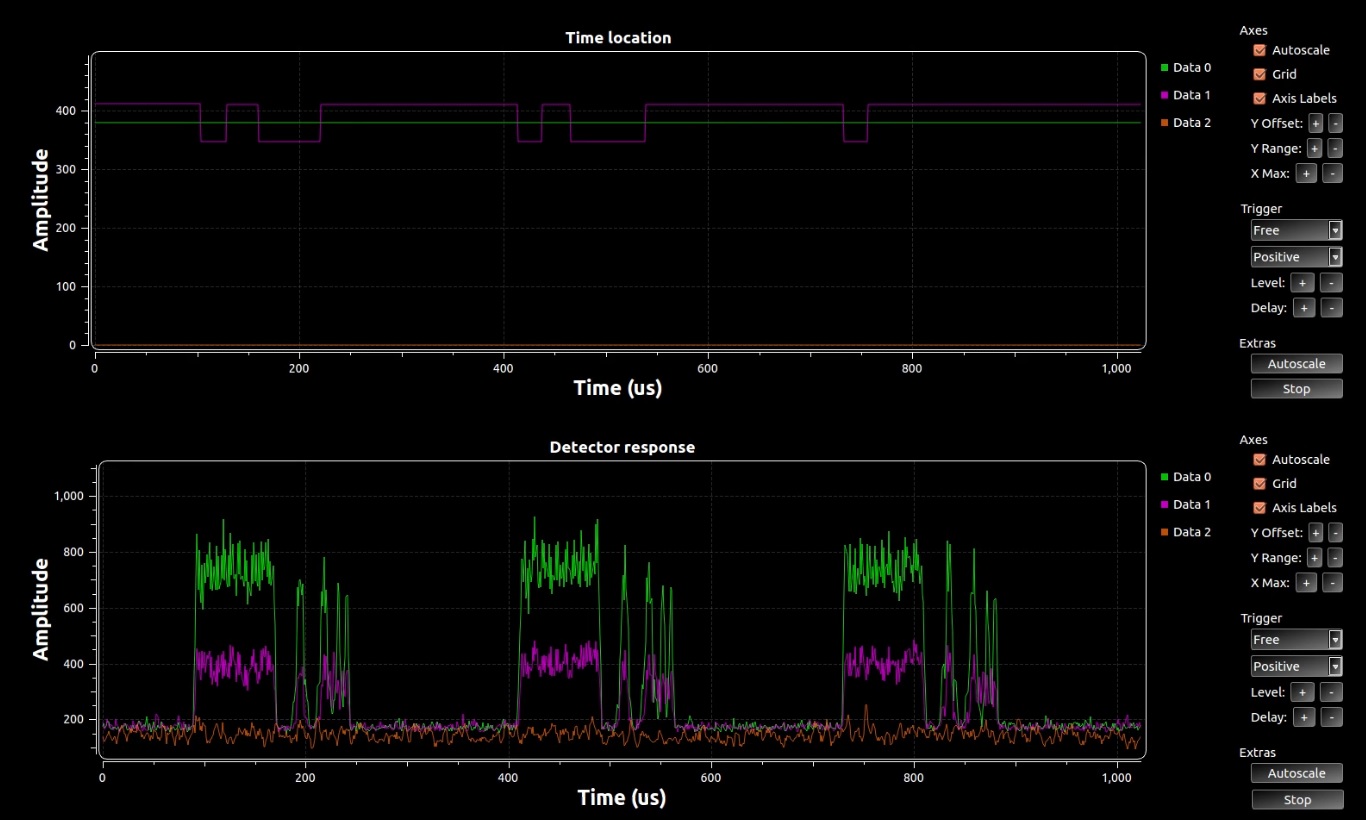
As we can see, only in the case of target key application a signal receiving is successful and synchronization is holding well. In the case of application of the key from the same set as target key detection is possible but data cannot be acquired due to time sync error. In the case of application of another random key detection of the desired signal is impossible, it recognized as noise.
Other tests relate to independent multi-user interaction. You can find it results in the video below.

